Reading the previous blog entry about port forwarding we have opened up a security hole that is now routing traffic to our Windows 10 Pro server behind our firewall. Crackers know this is port 1723 and will scan for it being open on your router. If you watch your router logs you will be surprised at how many attempts are being made to break into your network. I know you are a little fish but crackers consider (little fish) ripe targets! This begs the question of whether using a PAID service might not be a better solution for your small business. Opening up holes in a Windows 10 Pro server that is super important to your business might not be a good idea. Right now everything is OK because your VPN server is not listening but we are about to change that.
In our first post I highly encouraged you to watch Eli the Computer Guy’s video on what a
VPN is and how it works. You may discover that doing your own VPN is not going
to work for a verity of reasons which he describes very well. (See:
https://www.youtube.com/watch?v=q4P4BjjXghQ) For example, your ISP upload speed is very important if you are going to set up, use and manage your own VPN. Before we punch a hole in out SOHO local network and computer server make sure your set up and ISP speed are good enough for a Windows 10 Pro VPN.
Another thing to consider is server
uptime and power costs. When you, an employee, a family member are traveling
you have to have everything powered up and working. Not to mention your ISP can
change your modem IP at any time rendering all your hard work moot unless you
pay for a dynamic DNS service. A paid dynamic DNS service will map a domain name to
your modem and update the IP as your ISP does making sure you can always
connect to your network. Of course, if you have a computer savvy
person you can contact they can tell you the new DHCP ISP IP address by simply
typing, “What is my IP address?” in the Type or talk to search box and
give it to you over the phone, or have them log in to your router and view it there. (See:
http://dyn.com)
Therefore, once you have evaluated your
needs and have determined that you want to configure and manage your very own
Windows 10 Pro VPN, read on. For example, in my case I only need a VPN
occasionally while traveling or visiting a customer. I mostly use it with
hotspots to keep my laptop safe or to bypass a firewall or proxy so I can do
things on my home network that are not allowed where I am at. Paying for a
monthly VPN service does not make sense for my business and personal needs. If
you are a visual person watch this How To VPN YouTube video which is excellent. (See: https://www.youtube.com/watch?v=6ZCiXx6KYtA)
On your VPN server, if you have not
already done so, you will need to set up a standard user with very limited
privileges. In my book I detail how to do this on all your Windows 10 computers
because you should use a standard user ID when venturing out onto the infected
Internet. You can skip the following and go down to the Change Adapter Settings
but you should learn how to create a standard user the non-VPN way.
Click in
the lower left Type or talk to search box type user > click on
User Accounts Control Panel > select Manage another account
> click on Add a new user in the PC settings > under Other
people click on the + sign to Add someone else to this PC . Another
method you can employ is type Settings > click on Accounts
> click on Family & other people > click on the + sign to Add
someone else to this PC.
From here there is a multitude of ways you can add a user with the
default being Microsoft’s most invasive invasion of someone’s privacy. To
bypass all that and just add a local user which is all you need:
- At the bottom of the page, select I
don’t have this person’s sign-in information, and at the bottom of the next
page, select Add a user without a Microsoft account.
- On the Create an account for this
PC screen, enter a user name, password, and password hint, and then select Next.
You're done!
You are now ready to setup your VPN
server to use this account to connect to and tunnel into your local network. As
I said you could just start here where as you can see from the screen shot you
can click on the Add someone… button at the bottom and accomplish
everything we detailed above but then you wouldn’t have learned how to add a
Window 10 user the standard way. You can also do this using Computer Management
which is where you should check on what types of users exist on your PC. In the Type or Talk box type Computer
Management and open up the app > click on Local Users and Groups
> under Name on the right double click on Users > right
click on any user and select Properties and view their power. (See: http://www.howto-connect.com/windows-10-create-local-user-account-group-view)
Open up the Network and Sharing
Center by typing in
the Type or talk box type Network and Sharing > select Network and Sharing Center,
or go to your desktop > right click on the desktop Network icon >
arrow down to select Properties at the bottom of the menu.
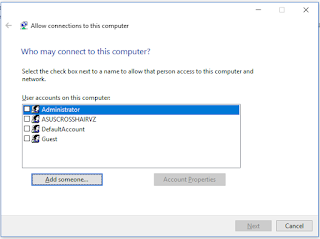
On the left menu click on Change
Adapter Settings > (NOTE: by default the File menu is not available,
click on the Organize drop down on the top left > arrow down to select Layout
> check Menu bar), click on the File menu and arrow down to
select New Incoming Connection… > the Allow connections to this
computer dialog will appear.
- Under
User accounts on this computer: select the user(s) that you want to have
access to your Windows VPN server, Next. (Warning: Make sure the accounts you select are NOT
administrative accounts).
- In the next dialog leave Through the Internet checked, Next > the
next dialog will ask you to check the type of networking for which you want to
allow incoming connections for > leave Internet Protocol Version 4
(TCP/IPv4) selected and I think you should check Internet Protocol Version
6 (TCP/IPv6). I don’t see anything wrong with enabling IPv6 for
incoming connections to your VPN server. If anything, we should uncheck IPv4
but let’s keep things simple and go with the default. Checking IPv6 may require a change in your
router to enable that.
Windows also selects File and Printer Sharing for Microsoft Networks
and QoS Packet Scheduler by default. The File and Printer Sharing
allows VPN connections to access shared files and printers on your network, and
QoS prioritizes network traffic, which will improve streaming video or playing
music through a VPN connection. As we discussed in detail in my book, QoS
provides an intelligent allocation of bandwidth between applications so if you
do not plan to use your VPN connection to stream or play music, disable this; the
same holds true for File and Printer Sharing. Any service you enable that is
not needed is a security hole that can be exploited.
- Click
on the Allow Access button at the bottom and now your VPN server will
allow incoming connections > the next screen will ask you to make note of
your Computer name: and suggests that you will need this to connect, Close.
You may have to refresh the screen by right clicking on the white space in the
window and selecting Refresh for the connection to show up.
- Windows
10 Pro then displays your Computer name: xxxxxxx which you have
to make note of because clients will need to know this to connect so write it
down > Close.
WARNING
|
Anytime you go mucking
around with your network settings things can go wrong. If you lose your
Network Connection try doing a system recovery back to your last known
settings.
|
If you right click on the
Incoming Connections icon that you
just created and select
Properties you will see three tabs at the top
titled
General,
Users and
Networking.
On
the General tab make sure that under Virtual private network, that
Allow others to make private connections to my computer… is checked >
on the Users tab check the users that you are going to allow to connect
> decide how you want to allow them to connect by checking Require all
users to secure their passwords and data or Always allow directly
connected devices such as handheld computers to connect without providing a
password.
Above is the bare minimum you should do to ensure the security of your
VPN server. If you really want to lock things down consider creating a port
forwarding rule that forwards a random "external port" to the
"internal port" 1723 that the Windows VPN server is listening on. This
will protect you from crackers who use automated hacking tools that attempt to
connect to VPN servers through the default port.
In my book's chapter on how to set up your router, we went into detail
about how to lock down your local area network. We did things, such as only
allowing wireless devices with known MAC addresses to connect to your router,
disabled SSID Broadcast, and much more. If you know you will be using the same
hotspot that has a static IP address we can configure our router to only accept
a connection from that specific IP address.
Log
in to the router as 'admin' > click
on the Advanced tab > on the left expand Advanced Setup and
select Remote Management > check Turn Remote Management On and
begin entering the IP addresses that you want to allow to connect to your
router and VPN server in your local network. You can also use
your VPN server firewall rules to only allow connection from specific IP
addresses.
Now you need to set up your VPN Windows 10 Pro firewall to accept connections on port 1723. The website
http://www.thewindowsclub.com/configure-vpn-connection-windows has an excellent description of how to do this but you will miss all the fun with cryptic Windows error messages getting your VPN client working... just kidding. After all, why go through all that pain when you have ThatCyberSecurityGuy, LLC to plow the road for you.
At this point I suggest you just disable your Windows 10 Pro server firewall and make sure you can establish a local client VPN connection behind your hardware firewall. With the client establishment we will cover all the things that can go wrong is you skip any of the steps I covered above.





