The Internet is stalking you. It is useful but it can become your worst enemy. As you now know, governments and corporations around the world expend vast resources and expense to spy upon your Internet use, phone conversations, email, GPS location and much more. Almost every facet of our daily lives are being scrutinized. Thousands of identity thieves, hackers, and criminal organizations are watching your Internet activity and installing malware on your Internet devices. You need my writing!
The Internet is Infected! The Ultimate Cyber Security Guide for Small Business and Home Computing!
If you find the information on this blog valuable you will find my upcoming three volume cyber security books infinitely more so! Visit my website at http://thatcybersecurityguy.com. My 8 years of research and 900 written pages are about much more than just cyber security as my writing presents valuable small business and general home computer knowledge. Visit me on Twitter @ThatCyberSecGuy. See the ACLU video "Invasion of the Data Snatchers" at YouTube to understand why you need my books and PDF files on the infected Internet.
Sunday, November 26, 2017
Syncing up Thunderbird to a sky drvie works but you need to clean house!
Therefore, only consider this cloud solution if you have a small amount of email with few attachments and only one or two accounts. In my case I still have a large amount of text only email and things sync up very quickly.
ThatCyberSecurityGuy, LLC
Kirk A. Ellis
Monday, October 23, 2017
How to snyc up a local Thunderbird email client to the cloud on multiple computers in small amounts
However, there are drawbacks to this that we will discuss, such as all of your computers being out-of-sync every time you turn them on. In addition, Thunderbird also has local configuration files signatures and account information that you will find hard to keep synced across all of your computers. For years I have used WinMerge (http://winmerge.org) with a USB drive in an attempt to keep all of the local files that Thunderbird uses in sync which has been a pain in my a$$. I also copied my local Thunderbird email files to my USB backups which is also painful and time consuming. There was also a lot on manual configuration to be performed on each computer to keep them in sync.
It is for these reasons that most people just log into their online email and manage everything at google.com or outlook.com, or one account on their smartphone, which I think is a mistake. If you have that power outage or are traveling to places unknown, you are completely cut off from your email. She had maintained all of her email with our ISP and when we moved, the ISP closed that account. What she did not understand was that when the account closed, she would lose all her email, all of her contacts, etc. and begged me to get them back, but no can do, not without a local copy backed up to your home computer! We also had hurricane IRMA when we lost power for five days!
Therefore, I set out to solve the best of both worlds for us all, so I will never again have to hear my wife cry about her email and contacts being lost. I also don't want to waste my time for years to come, manually syncing configuration files on all my computers that are running the Thunderbird email client. The first problem I ran into was finding all the local Thunderbird files and then moving them to my sky drive. Directions on how to do this will be coming in my next blog entry, as I ran into a few problems syncing my first two computers.
NOTE: You will have to assess whether or not your email files will fit into your sky drive by right-clicking on the directory and selecting Properties to see just how big your email files have become. It is surprising the amount of junk email we have hanging around.
In my case, everything fit so I moved it all thinking that I had a solution to the Thunderbird local email client, now sky drive problem. However, my computers began taking large amounts of time syncing up to my Google Sky Drive, as my local (now sky) files were gigabytes in size. Thunderbird constantly reshapes its local .msf storage files that house your email, thus causing constant syncing to take place as you read, delete and compact these files.
Also understand that Thunderbird is syncing with its configured email servers as local email accounts/files download and adjust to your ISP accounts. This causes a double sync in where your email client is syncing to your sky drive because your email client just synced which makes this solution sound impossible (round and round) unless you have an incredibly FAST Internet connection and in that thought you are correct, somewhat.
As a result before I can finish this project I had to go through about 7 years of email and delete and compact everything I could before making this all work. Once I got the Thunderbird .msf files down to a small size this worked beautifully! Please understand this process of deleting email, compacting files and then syncing them up again is painful but liberating (like starting a whole new life!). I had to relive deaths in the family, arguments, emails from my editor, bad news from my master tax preparer, and so much more. However, I kept at it and after each evening of work my sync time is got shorter and shorter with my Gigabyte Internet connection making this a very viable and awesome solution to a multiple email account local/sky/IMAP former problem.
WARNING: Do not enter into this project unless you are willing to spend the time to delete a ton of old email. If you do not, you will forever see your Thunderbird email and files continuously syncing up both to your email servers and to your cloud drive. If you don't clean house you will find yourself unable to even send an email while minutes or hours of syncing takes place. In my case it took me weeks to delete all my old email and compact the Thunderbird folders to a suitable size but what a refreshing experience it was!
Also, even though Uncle Sam keeps all your email for you entire lifetime at U.S. Taxpayer expense (why U.S. citizens put up with this is unknown) your ISP does not. By cleaning out all your old email you get back a small measure of privacy as this correspondence can no longer be read by the whole world! You ISP has to maintain it for a while but they will eventually purge it from their databases.
Sunday, February 5, 2017
How to Setup your Windows 10 Pro VPN Client to use at Hotspots and behind firewalls Everywhere
Things are very exciting now that we have 2/3 of the SOHO VPN pie complete. Our router and Windows 10 server configurations are complete. We now have to configure our client as an outgoing VPN connection. Be sure to read all of this blog entry because things get a little tricky. We will need our ISP provided IP address which can be obtained by logging into our router or by opening up Microsoft Edge and typing (What is my IP?). We are going to need this later to configure this VPN client.
Now things get really cool as we are going to configure a local VPN client to test everything out. This eliminates the router as a possible connection point of failure before we even venture out on to the WAN and use infected hotspots. Bring up the Network and Sharing Center by typing in the Type or talk box. Select Set up a new connection or network > on the Choose a connection option screen choose Connect to a workplace, Set up a dial-up or VPN connection to your workplace , Next > On the How do you want to connect? Screen select Use my Internet connection (VPN), Connect using a virtual private network (VPN) connection through the Internet. > on the Type the Internet address to connect to screen we can enter the IPv4 or IPv6 local IP address (I prefer IPv6), leave everything else at the default value > click on the Create button lower right.
Now let us test everything out to see if it is working locally. Bring up the Network and Sharing center and click on the Change adapter settings link on the left > double click on VPN Connection, WAN Miniport (IKEv2) on the VPN screen double click on VPN Connection which was the default name we accepted. NOTE: We could have gotten here by just typing VPN in the Type or talk box. Click on the Connect button > this will bring up the Sign in screen where you will enter the username and password you configured on the server > you will see Verifying your sign-in info and now you are done OR NOT! This is the tricky part I described earlier.
You can beat your head into a wall searching for this error but from my experience with Windows 7, this was a 720 error code and we have to configure the VPN server to assign IP addresses to incoming VPN connections rather than allowing them to be assigned by our DHCP router. Make sure your IP range is one not being used by devices in your LAN.
We are done right? Well not really, because we disabled Windows 10 Pro firewall and rebooted out VPN server. It is now broken and wide open to crackers. You can test all this out by enabling your firewall again, rebooting your VPN server as you will see The remote connection was not made because the attempted VPN tunnels failed... error message again. Therefore, we have to figure out how to allow our client VPN through our Windows 10 Pro firewall.
How To Setup your Windows 10 VPN Server behind your Router Hardware Firewall
- At the bottom of the page, select I don’t have this person’s sign-in information, and at the bottom of the next page, select Add a user without a Microsoft account.
- On the Create an account for this PC screen, enter a user name, password, and password hint, and then select Next. You're done!
Open up the Network and Sharing Center by typing in the Type or talk box type Network and Sharing > select Network and Sharing Center, or go to your desktop > right click on the desktop Network icon > arrow down to select Properties at the bottom of the menu.
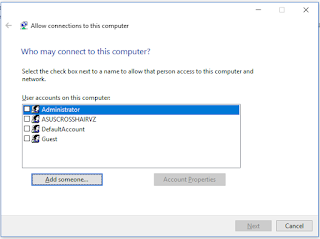
- Under User accounts on this computer: select the user(s) that you want to have access to your Windows VPN server, Next. (Warning: Make sure the accounts you select are NOT administrative accounts).
- In the next dialog leave Through the Internet checked, Next > the next dialog will ask you to check the type of networking for which you want to allow incoming connections for > leave Internet Protocol Version 4 (TCP/IPv4) selected and I think you should check Internet Protocol Version 6 (TCP/IPv6). I don’t see anything wrong with enabling IPv6 for incoming connections to your VPN server. If anything, we should uncheck IPv4 but let’s keep things simple and go with the default. Checking IPv6 may require a change in your router to enable that.
- Click on the Allow Access button at the bottom and now your VPN server will allow incoming connections > the next screen will ask you to make note of your Computer name: and suggests that you will need this to connect, Close. You may have to refresh the screen by right clicking on the white space in the window and selecting Refresh for the connection to show up.
- Windows 10 Pro then displays your Computer name: xxxxxxx which you have to make note of because clients will need to know this to connect so write it down > Close.
WARNING
|
Anytime you go mucking
around with your network settings things can go wrong. If you lose your
Network Connection try doing a system recovery back to your last known
settings.
|
Above is the bare minimum you should do to ensure the security of your VPN server. If you really want to lock things down consider creating a port forwarding rule that forwards a random "external port" to the "internal port" 1723 that the Windows VPN server is listening on. This will protect you from crackers who use automated hacking tools that attempt to connect to VPN servers through the default port.
Now you need to set up your VPN Windows 10 Pro firewall to accept connections on port 1723. The website http://www.thewindowsclub.com/configure-vpn-connection-windows has an excellent description of how to do this but you will miss all the fun with cryptic Windows error messages getting your VPN client working... just kidding. After all, why go through all that pain when you have ThatCyberSecurityGuy, LLC to plow the road for you.
At this point I suggest you just disable your Windows 10 Pro server firewall and make sure you can establish a local client VPN connection behind your hardware firewall. With the client establishment we will cover all the things that can go wrong is you skip any of the steps I covered above.